TorrentLocker Ransomware variation written to specifically target Japanese usersAbout TorrentLockerThe attack
About TorrentLocker
This new type of ransomware is a sibling of CryptoLocker and CrptoWall ransomware and uses communicates with its command and control server using Tor anonymiser network. TorrentLocker uses themes and naming from CryptoLocker and CryptoWall ransomware, but is very different at the code level and believed to be a new strain of ransomware. The malware first connects to a command and control (C&C) server over secure communications and exchanges a certificate before encrypting the malware. The malware uses the Rijndael algorithm for file encryption. This is a symmetric cipher and will use a password either stored locally or retrieved from the remote attackers’ server for encryption.
The attack
Ransomware generally spread through as many mediums as possible trying to infect unsuspecting users, however the most preferred medium for the cyber criminals is spear phishing. The malware is laden in a innocuous email as an attachment which the victim downloads thinking it to be a genuine file. Once a ransom ware has been downloaded onto a machine, it goes on to encrypt all the files it has been commanded to do via program and request payment – usually in Bitcoins – to decrypt the files, thus making user data the hostage. This particular ransom ware also works the same way with the addition that all instructions are written in Japanese.
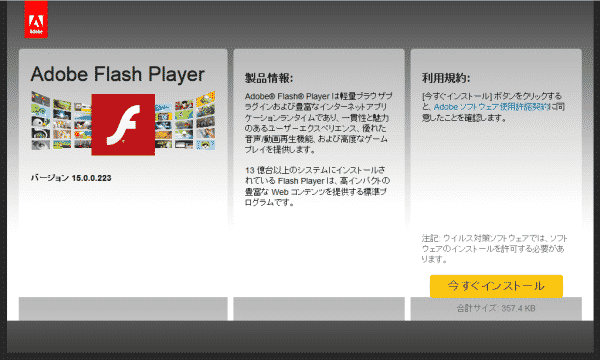
The malware is spread via the phishing page as given in the above picture which displays a fake Adobe Flash Player installer page. If a user clicks on the link in yellow to download this fake Flash Player, they are prompted to download and execute a setup file to install the plugin. However, the file is not digitally signed, nor does not it contain the typical icon used in Flash Player installers. These two facts suggest that it is a fake malware laden application which only keen users will be able to spot the difference. Once the file is downloaded and installed, the ransom ware gets to task encrypting the user’s data.
Once the malware has finished its job, this screen is shown to the user. The message then asks the user to pay in order to unlock their files. The demanded ransom ranges from 40,000 yen to 300,000 yen (approximately US$500 to US$3,600). Japan is fast approaching its new year’s holiday which is an opportune time for the cybercriminals to strike. The attacker probably wants to make the most use of unsuspecting users browsing the internet. Symantec has the following recommendations to avoid or mitigate ransomware infections:
Update the software, operating system, and browser plugins on your computer to prevent attackers from exploiting known vulnerabilities. Use comprehensive security software, such as Norton Security, to protect yourself from cyber criminals. Regularly back up any files stored on your computer. If your computer has been compromised with ransomware, then these files can be restored once the malware is removed from the computer. Never pay the ransom. There’s no guarantee that the attacker will decrypt the files as promised once they receive payment.